
Late last year, Velodyne LiDAR Inc., the world leader in 3D vision systems for autonomous vehicles, created a partnership with BoE Systems.
Velodyne integrated its VLP-16 Puck and Puck LITE 3D LiDAR sensors into BoE Systems’ UAV fleet for geospatial data collection and analysis.
With this integration, BoE Systems now offers full 360° imaging of geography and equipment that serve a multitude of industries.
These services meet a growing need for quick, safe, and accurate aerial inspections. Such industries, include: transportation, utilities, telecommunications/infrastructure, construction, aggregate, forestry, and agriculture.
Tailored Solutions
BoE Systems acquires imaging data, processes it, and provides customers tailored analysis and inspection reports. This information allows companies to address immediate as well as future needs and compliance issues.
In addition, BoE Systems’ proprietary hardware and software integrations provide highly detailed digital maps. Such detail allows for the development of highly accurate flood models, drainage analysis, Building Information Modeling (BIM), contour mapping, and more.
“UAV mapping is a nascent industry that has quickly evolved with the adoption of LiDAR sensor technology,” said Mike Jellen, President and Chief Commercial Officer, Velodyne LiDAR. “With BoE Systems’ integration of Velodyne’s advanced VLP-16 Puck and Puck LITE sensors, the result is an incredibly valuable service that quickly and accurately maps geography and equipment to save customers critical man-hours, cost, and effort.”
“BoE Systems’ hardware and software integrations leverage cutting edge technology like Velodyne’s VLP-16 LiDAR sensors to produce highly accurate 3-dimensional environmental models for industry professionals,” said Jason Littrell, President, BoE Systems. “Those professionals appreciate that our systems can do the job quickly, safely, accurately, and without breaking the bank.”
About Velodyne LiDAR
Founded in 1983, Velodyne is a technology company known worldwide for its real-time 3D LiDAR sensors. The company evolved after founder/inventor David Hall developed the HDL-64 Solid-State Hybrid LiDAR sensor in 2005. Velodyne emerged as the unmatched market leader of real-time 3D vision systems.
Its products range from the high-performance, surround view UltraPuck™ VLP-32, classic HDL-32/64 and cost-effective VLP-16, to the upcoming, hidden Velarray™. Velodyne’s rich suite of perception software and algorithms are the key enablers of its perception systems.
About BoE Systems
BoE Systems integrates cutting-edge hardware and software to provide highly accurate geospatial data collection solutions. BOE's drone-based aerial LiDAR systems create detail-rich 3D models for a variety of industries.
Analytics are applied to determine critical data points such as geodetic locations, slope identification, point-to-point measurements, volumetrics, and more. BoE models are perfect for creating digital elevation models, overlaying contour lines. Additionally, these models even support predictive analytics such as flooding and drainage analysis.
 Altavian, Inc., announced they were awarded a $250MM Indefinite Delivery, Indefinite Quantity contract with the US Army.
With this award, Altavian now supports the largest small UAS program in the world. It exists under the Program Executive Office Aviation, Products Office for Tactical Unmanned Aircraft (TUAS),
The US Army Family of Systems, Unmanned Aircraft Systems (FoSUAS) includes the RQ-11, the RQ-20. It supports control and communications equipment, and other technologies fielded over the contract period of performance.
All systems are for a single, dismounted war-fighter. The design enables the individual to carry, assemble, and deploy the system for immediate over-the-hill surveillance and reconnaissance.
Altavian, Inc., announced they were awarded a $250MM Indefinite Delivery, Indefinite Quantity contract with the US Army.
With this award, Altavian now supports the largest small UAS program in the world. It exists under the Program Executive Office Aviation, Products Office for Tactical Unmanned Aircraft (TUAS),
The US Army Family of Systems, Unmanned Aircraft Systems (FoSUAS) includes the RQ-11, the RQ-20. It supports control and communications equipment, and other technologies fielded over the contract period of performance.
All systems are for a single, dismounted war-fighter. The design enables the individual to carry, assemble, and deploy the system for immediate over-the-hill surveillance and reconnaissance.

 Recently, FT Technologies updated the 722 and 742 digital wind sensors.
Now, these models can read acoustic temperature as well as wind speed and wind direction.
The air temperature is derived from the operating frequency of the sensor. It has an accuracy of ±1°C.
Recently, FT Technologies updated the 722 and 742 digital wind sensors.
Now, these models can read acoustic temperature as well as wind speed and wind direction.
The air temperature is derived from the operating frequency of the sensor. It has an accuracy of ±1°C.
 Late last year, Velodyne LiDAR Inc., the world leader in 3D vision systems for autonomous vehicles, created a partnership with BoE Systems.
Velodyne integrated its VLP-16 Puck and Puck LITE 3D LiDAR sensors into BoE Systems’ UAV fleet for geospatial data collection and analysis.
With this integration, BoE Systems now offers full 360° imaging of geography and equipment that serve a multitude of industries.
These services meet a growing need for quick, safe, and accurate aerial inspections. Such industries, include: transportation, utilities, telecommunications/infrastructure, construction, aggregate, forestry, and agriculture.
Late last year, Velodyne LiDAR Inc., the world leader in 3D vision systems for autonomous vehicles, created a partnership with BoE Systems.
Velodyne integrated its VLP-16 Puck and Puck LITE 3D LiDAR sensors into BoE Systems’ UAV fleet for geospatial data collection and analysis.
With this integration, BoE Systems now offers full 360° imaging of geography and equipment that serve a multitude of industries.
These services meet a growing need for quick, safe, and accurate aerial inspections. Such industries, include: transportation, utilities, telecommunications/infrastructure, construction, aggregate, forestry, and agriculture.


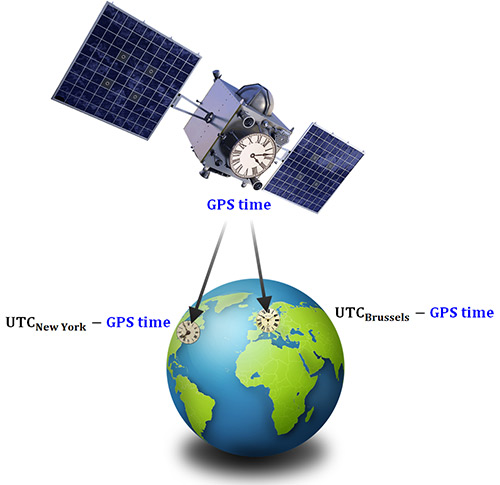
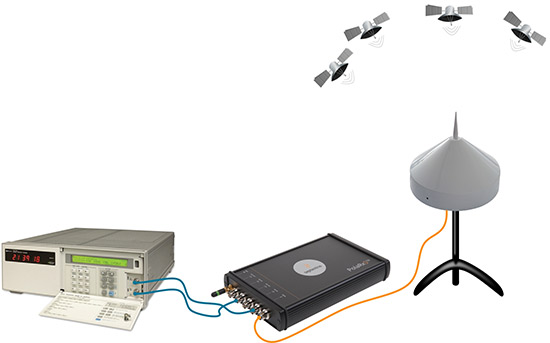


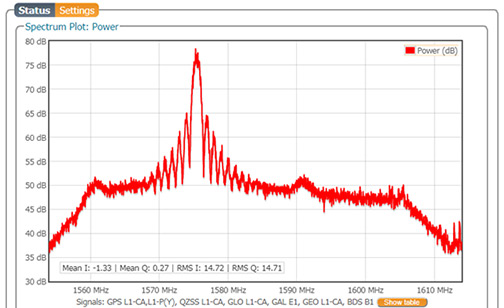
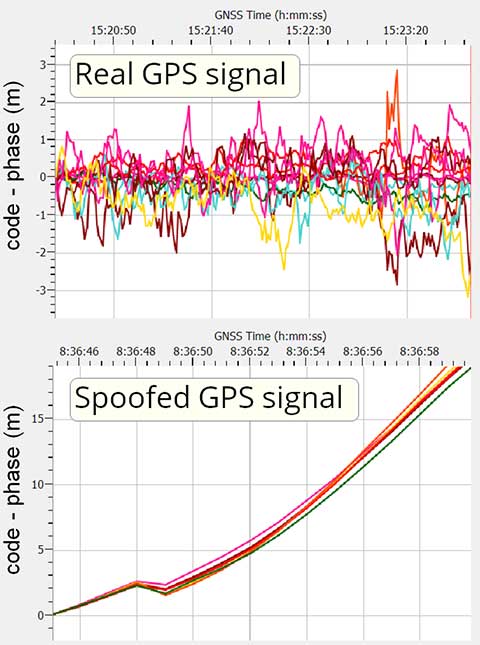
 Recently, MicroPilot announced that their autopilot now supports transitioning VTOL drones.
MicroPilot autopilots already fly a wide range of UAVs, including: fixed-wings, multi-rotors, helicopters and even tail sitters.
Now, manufacturers of transitioning UAV drones have the option of a professional autopilot known for its reliability.
Recently, MicroPilot announced that their autopilot now supports transitioning VTOL drones.
MicroPilot autopilots already fly a wide range of UAVs, including: fixed-wings, multi-rotors, helicopters and even tail sitters.
Now, manufacturers of transitioning UAV drones have the option of a professional autopilot known for its reliability.
